Neelabh Mam
2014-07-24 19:20:13 UTC
Greetings,
I have been using this version for almost 2 months now and I must say that
somehow my setup managed to have it crashed 2 times. This time around, I
was able to capture it. Also, some how I keep getting the attached error
when I try to update via the "Help" menu item, whats the deal with this ?
Please redirect if this is not the correct forum, Thank you.
PS: I do have mfh dump saved in case you'd want me to upload it to a public
ftp server, thanks again.
0:009> !analyze -v
*******************************************************************************
*
*
* Exception Analysis
*
*
*
*******************************************************************************
EXCEPTION_RECORD: ffffffffffffffff -- (.exr 0xffffffffffffffff)
ExceptionAddress: 0000000077b0320e (ntdll!RtlFreeHeap+0x000000000000004e)
ExceptionCode: c0000005 (Access violation)
ExceptionFlags: 00000000
NumberParameters: 2
Parameter[0]: 0000000000000000
Parameter[1]: 000000000000003f
Attempt to read from address 000000000000003f
PROCESS_NAME: VirtualBox.exe
ERROR_CODE: (NTSTATUS) 0xc0000005 - The instruction at 0x%08lx referenced
memory at 0x%08lx. The memory could not be %s.
EXCEPTION_CODE: (NTSTATUS) 0xc0000005 - The instruction at 0x%08lx
referenced memory at 0x%08lx. The memory could not be %s.
EXCEPTION_PARAMETER1: 0000000000000000
EXCEPTION_PARAMETER2: 000000000000003f
READ_ADDRESS: 000000000000003f
FOLLOWUP_IP:
ntdll!RtlFreeHeap+4e
00000000`77b0320e 807b0f05 cmp byte ptr [rbx+0Fh],5
MOD_LIST: <ANALYSIS/>
NTGLOBALFLAG: 0
APPLICATION_VERIFIER_FLAGS: 0
ADDITIONAL_DEBUG_TEXT: Enable Pageheap/AutoVerifer
FAULTING_THREAD: 0000000000001388
DEFAULT_BUCKET_ID: HEAP_CORRUPTION
PRIMARY_PROBLEM_CLASS: HEAP_CORRUPTION
BUGCHECK_STR:
APPLICATION_FAULT_HEAP_CORRUPTION_NULL_CLASS_PTR_DEREFERENCE_INVALID_POINTER_READ
LAST_CONTROL_TRANSFER: from 00000000778b1a4a to 0000000077b0320e
STACK_TEXT:
00000000`0532f980 00000000`778b1a4a : 00000000`03b913d0 00000000`fffffc85
00000000`03b913d0 000007fe`e90007f2 : ntdll!RtlFreeHeap+0x4e
00000000`0532fa00 00000000`71bf8d94 : 00000000`0532fbb8 00000000`0532fb50
00000000`03b913d0 000007fe`e8ff6cc3 : kernel32!HeapFree+0xa
00000000`0532fa30 000007fe`e8e84c3f : 00000000`00000001 00000000`03b913d0
00000000`00000075 00000000`00000000 : msvcr100!free+0x1c
00000000`0532fa60 000007fe`e8ea1aad : 00000000`00000000 00000000`00000000
00000000`00000001 00000000`03afe9d0 : VBoxRT!RTMemFree+0xf
00000000`0532fa90 00000001`3fb54d74 : 00000000`00000998 00000000`0532fcb0
00000000`0532fbb0 00000000`71bf8d17 : VBoxRT!RTHttpCertDigest+0x16d
00000000`0532fb10 00000001`3fb55643 : 00000000`03b7ac80 00000000`03b7ac80
00000000`0532fbd9 00000000`03b7ac80 : VirtualBox!TrustedMain+0x233404
00000000`0532fb90 00000001`3fb564c6 : 00000000`00000000 00000000`00000000
00000000`00000000 00000000`03b7ac80 : VirtualBox!TrustedMain+0x233cd3
00000000`0532fc40 00000001`3fb56a71 : 00000000`00000000 00000000`03b397e0
00000000`03c972c0 00000000`02490f50 : VirtualBox!TrustedMain+0x234b56
00000000`0532fca0 00000001`3fb57006 : 00000000`03b397e0 00000000`03b397e0
00000000`00000002 00000000`025c3d60 : VirtualBox!TrustedMain+0x235101
00000000`0532fcf0 00000001`3fb57852 : 00000000`03b397e0 00000000`03b4d200
00000000`03b397e0 00000000`03b397e0 : VirtualBox!TrustedMain+0x235696
00000000`0532fd30 00000000`718d61e7 : 00000000`023ea998 00000000`023ea998
00000000`023ea910 00000000`03b397e0 : VirtualBox!TrustedMain+0x235ee2
00000000`0532fd60 00000000`71bb1d9f : 00000000`03acc010 00000000`024e1bd0
00000000`00000000 00000000`00000000 : QtCoreVBox4!QThread::setPriority+0x307
00000000`0532fdb0 00000000`71bb1e3b : 00000000`71c42ac0 00000000`024e1bd0
00000000`00000000 00000000`00000000 : msvcr100!endthreadex+0x43
00000000`0532fde0 00000000`778a59ed : 00000000`00000000 00000000`00000000
00000000`00000000 00000000`00000000 : msvcr100!endthreadex+0xdf
00000000`0532fe10 00000000`77adc541 : 00000000`00000000 00000000`00000000
00000000`00000000 00000000`00000000 : kernel32!BaseThreadInitThunk+0xd
00000000`0532fe40 00000000`00000000 : 00000000`00000000 00000000`00000000
00000000`00000000 00000000`00000000 : ntdll!RtlUserThreadStart+0x1d
STACK_COMMAND: ~9s; .ecxr ; kb
SYMBOL_NAME: heap_corruption!heap_corruption
FOLLOWUP_NAME: MachineOwner
MODULE_NAME: heap_corruption
IMAGE_NAME: heap_corruption
DEBUG_FLR_IMAGE_TIMESTAMP: 0
FAILURE_BUCKET_ID: HEAP_CORRUPTION_c0000005_heap_corruption!heap_corruption
BUCKET_ID:
X64_APPLICATION_FAULT_HEAP_CORRUPTION_NULL_CLASS_PTR_DEREFERENCE_INVALID_POINTER_READ_heap_corruption!heap_corruption
WATSON_STAGEONE_URL:
http://watson.microsoft.com/StageOne/VirtualBox_exe/4_3_12_0/5375fea0/ntdll_dll/6_1_7601_18247/521eaf24/c0000005/0005320e.htm?Retriage=1
Followup: MachineOwner
---------
0:009> lmvm virtualbox
start end module name
00000001`3f920000 00000001`4018e000 VirtualBox (export symbols)
VirtualBox.exe
Loaded symbol image file: VirtualBox.exe
Image path: C:\Program Files\Oracle\VirtualBox\VirtualBox.exe
Image name: VirtualBox.exe
Timestamp: Fri May 16 17:33:44 2014 (5375FEA0)
CheckSum: 00875E54
ImageSize: 0086E000
File version: 4.3.12.0
Product version: 4.3.12.0
File flags: 0 (Mask 3F)
File OS: 4 Unknown Win32
File type: 1.0 App
File date: 00000000.00000000
Translations: 0409.04e4
CompanyName: Oracle Corporation
ProductName: Oracle VM VirtualBox
InternalName: VirtualBox.exe
OriginalFilename: VirtualBox.exe
ProductVersion: 4.3.12.r93733
FileVersion: 4.3.12.93733
FileDescription: Oracle VM VirtualBox Manager
LegalCopyright: Copyright (C) 2009-2014 Oracle Corporation
-------------- next part --------------
An HTML attachment was scrubbed...
URL: http://www.virtualbox.org/pipermail/vbox-dev/attachments/20140725/bfb35b9b/attachment-0001.html
-------------- next part --------------
A non-text attachment was scrubbed...
Name: Capture.PNG
Type: image/png
Size: 31982 bytes
Desc: not available
Url : Loading Image...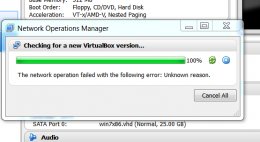
I have been using this version for almost 2 months now and I must say that
somehow my setup managed to have it crashed 2 times. This time around, I
was able to capture it. Also, some how I keep getting the attached error
when I try to update via the "Help" menu item, whats the deal with this ?
Please redirect if this is not the correct forum, Thank you.
PS: I do have mfh dump saved in case you'd want me to upload it to a public
ftp server, thanks again.
0:009> !analyze -v
*******************************************************************************
*
*
* Exception Analysis
*
*
*
*******************************************************************************
EXCEPTION_RECORD: ffffffffffffffff -- (.exr 0xffffffffffffffff)
ExceptionAddress: 0000000077b0320e (ntdll!RtlFreeHeap+0x000000000000004e)
ExceptionCode: c0000005 (Access violation)
ExceptionFlags: 00000000
NumberParameters: 2
Parameter[0]: 0000000000000000
Parameter[1]: 000000000000003f
Attempt to read from address 000000000000003f
PROCESS_NAME: VirtualBox.exe
ERROR_CODE: (NTSTATUS) 0xc0000005 - The instruction at 0x%08lx referenced
memory at 0x%08lx. The memory could not be %s.
EXCEPTION_CODE: (NTSTATUS) 0xc0000005 - The instruction at 0x%08lx
referenced memory at 0x%08lx. The memory could not be %s.
EXCEPTION_PARAMETER1: 0000000000000000
EXCEPTION_PARAMETER2: 000000000000003f
READ_ADDRESS: 000000000000003f
FOLLOWUP_IP:
ntdll!RtlFreeHeap+4e
00000000`77b0320e 807b0f05 cmp byte ptr [rbx+0Fh],5
MOD_LIST: <ANALYSIS/>
NTGLOBALFLAG: 0
APPLICATION_VERIFIER_FLAGS: 0
ADDITIONAL_DEBUG_TEXT: Enable Pageheap/AutoVerifer
FAULTING_THREAD: 0000000000001388
DEFAULT_BUCKET_ID: HEAP_CORRUPTION
PRIMARY_PROBLEM_CLASS: HEAP_CORRUPTION
BUGCHECK_STR:
APPLICATION_FAULT_HEAP_CORRUPTION_NULL_CLASS_PTR_DEREFERENCE_INVALID_POINTER_READ
LAST_CONTROL_TRANSFER: from 00000000778b1a4a to 0000000077b0320e
STACK_TEXT:
00000000`0532f980 00000000`778b1a4a : 00000000`03b913d0 00000000`fffffc85
00000000`03b913d0 000007fe`e90007f2 : ntdll!RtlFreeHeap+0x4e
00000000`0532fa00 00000000`71bf8d94 : 00000000`0532fbb8 00000000`0532fb50
00000000`03b913d0 000007fe`e8ff6cc3 : kernel32!HeapFree+0xa
00000000`0532fa30 000007fe`e8e84c3f : 00000000`00000001 00000000`03b913d0
00000000`00000075 00000000`00000000 : msvcr100!free+0x1c
00000000`0532fa60 000007fe`e8ea1aad : 00000000`00000000 00000000`00000000
00000000`00000001 00000000`03afe9d0 : VBoxRT!RTMemFree+0xf
00000000`0532fa90 00000001`3fb54d74 : 00000000`00000998 00000000`0532fcb0
00000000`0532fbb0 00000000`71bf8d17 : VBoxRT!RTHttpCertDigest+0x16d
00000000`0532fb10 00000001`3fb55643 : 00000000`03b7ac80 00000000`03b7ac80
00000000`0532fbd9 00000000`03b7ac80 : VirtualBox!TrustedMain+0x233404
00000000`0532fb90 00000001`3fb564c6 : 00000000`00000000 00000000`00000000
00000000`00000000 00000000`03b7ac80 : VirtualBox!TrustedMain+0x233cd3
00000000`0532fc40 00000001`3fb56a71 : 00000000`00000000 00000000`03b397e0
00000000`03c972c0 00000000`02490f50 : VirtualBox!TrustedMain+0x234b56
00000000`0532fca0 00000001`3fb57006 : 00000000`03b397e0 00000000`03b397e0
00000000`00000002 00000000`025c3d60 : VirtualBox!TrustedMain+0x235101
00000000`0532fcf0 00000001`3fb57852 : 00000000`03b397e0 00000000`03b4d200
00000000`03b397e0 00000000`03b397e0 : VirtualBox!TrustedMain+0x235696
00000000`0532fd30 00000000`718d61e7 : 00000000`023ea998 00000000`023ea998
00000000`023ea910 00000000`03b397e0 : VirtualBox!TrustedMain+0x235ee2
00000000`0532fd60 00000000`71bb1d9f : 00000000`03acc010 00000000`024e1bd0
00000000`00000000 00000000`00000000 : QtCoreVBox4!QThread::setPriority+0x307
00000000`0532fdb0 00000000`71bb1e3b : 00000000`71c42ac0 00000000`024e1bd0
00000000`00000000 00000000`00000000 : msvcr100!endthreadex+0x43
00000000`0532fde0 00000000`778a59ed : 00000000`00000000 00000000`00000000
00000000`00000000 00000000`00000000 : msvcr100!endthreadex+0xdf
00000000`0532fe10 00000000`77adc541 : 00000000`00000000 00000000`00000000
00000000`00000000 00000000`00000000 : kernel32!BaseThreadInitThunk+0xd
00000000`0532fe40 00000000`00000000 : 00000000`00000000 00000000`00000000
00000000`00000000 00000000`00000000 : ntdll!RtlUserThreadStart+0x1d
STACK_COMMAND: ~9s; .ecxr ; kb
SYMBOL_NAME: heap_corruption!heap_corruption
FOLLOWUP_NAME: MachineOwner
MODULE_NAME: heap_corruption
IMAGE_NAME: heap_corruption
DEBUG_FLR_IMAGE_TIMESTAMP: 0
FAILURE_BUCKET_ID: HEAP_CORRUPTION_c0000005_heap_corruption!heap_corruption
BUCKET_ID:
X64_APPLICATION_FAULT_HEAP_CORRUPTION_NULL_CLASS_PTR_DEREFERENCE_INVALID_POINTER_READ_heap_corruption!heap_corruption
WATSON_STAGEONE_URL:
http://watson.microsoft.com/StageOne/VirtualBox_exe/4_3_12_0/5375fea0/ntdll_dll/6_1_7601_18247/521eaf24/c0000005/0005320e.htm?Retriage=1
Followup: MachineOwner
---------
0:009> lmvm virtualbox
start end module name
00000001`3f920000 00000001`4018e000 VirtualBox (export symbols)
VirtualBox.exe
Loaded symbol image file: VirtualBox.exe
Image path: C:\Program Files\Oracle\VirtualBox\VirtualBox.exe
Image name: VirtualBox.exe
Timestamp: Fri May 16 17:33:44 2014 (5375FEA0)
CheckSum: 00875E54
ImageSize: 0086E000
File version: 4.3.12.0
Product version: 4.3.12.0
File flags: 0 (Mask 3F)
File OS: 4 Unknown Win32
File type: 1.0 App
File date: 00000000.00000000
Translations: 0409.04e4
CompanyName: Oracle Corporation
ProductName: Oracle VM VirtualBox
InternalName: VirtualBox.exe
OriginalFilename: VirtualBox.exe
ProductVersion: 4.3.12.r93733
FileVersion: 4.3.12.93733
FileDescription: Oracle VM VirtualBox Manager
LegalCopyright: Copyright (C) 2009-2014 Oracle Corporation
-------------- next part --------------
An HTML attachment was scrubbed...
URL: http://www.virtualbox.org/pipermail/vbox-dev/attachments/20140725/bfb35b9b/attachment-0001.html
-------------- next part --------------
A non-text attachment was scrubbed...
Name: Capture.PNG
Type: image/png
Size: 31982 bytes
Desc: not available
Url : Loading Image...